In this article I present the recent findings of the malicious software "Hive" uncovered by the Wikileaks foundation.

I am the eagle watching over you and for you own safety
image source
CIAs remote data collection mechanism
Just 3 weeks ago Wikileaks made yet another important contribution to the database of publicly available classified files.
Unveiling the mischief of the CIA has been an important past time of Wikileaks in 2017 and after uncovering 23 different secret tools this year (Vault 7) - in this batch (Vault 8) - the project HIVE is added to the list.
The leaked files contain information about a significant component of the CIA software architecture: The Hive is a Command-and-Control Server that communicates with malware on infected computers and allows the agency to send commands to the targets to extract further information.
You can imagine the Hive as a an command center that governs over multiple infected users simultaneously.
Let's learn from the pro's
The architecture is designed to prevent the public associating malware to the CIA. To ensure this, the Control Server includes a public website that acts as a decoy and a multi-level VPN stage.
"Using Hive even if an implant is discovered on a target computer, attributing it to the CIA is difficult by just looking at the communication of the malware with other servers on the internet"
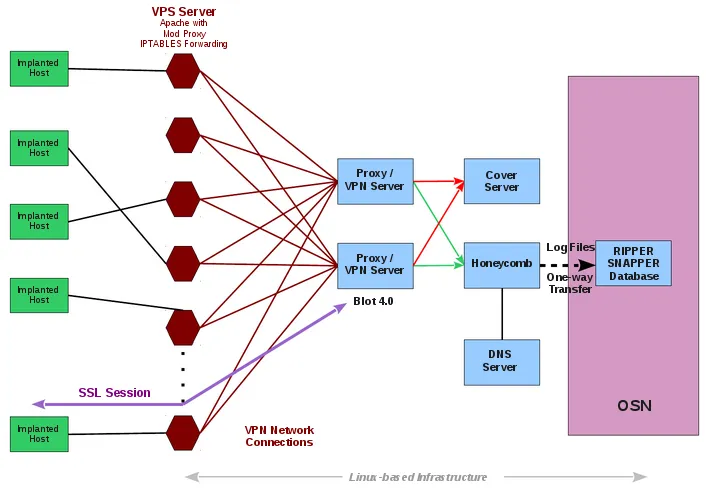
image source
In the picture presented by Wikileaks, you can follow how it works. On the far left you have infected user machines and on the far right you have the CIA command center. In the middle, the blue boxes are components of the clever multiple VPN stage that is used to deceive anyone snooping around for evidence.
A key component is the cover server: The fake domain displays "innocent" content to a user who might visit the domain by chance. A regular visitor would not suspect that something is hidden beneath the normal website. The delicate feature is only visible to technically sophisticated people - the server has the HTTPS Optional Client Authentication enabled. The obscure feature is barely used elsewhere - it allows users browsing a website to authenticate themselves. (Usually it is the other way around: The website is requesting you to perform an authentication procedure, not you offering it.)
This is how the Hive can differentiate between implant traffic and regular traffic; Regular users will be redirected to the fake website, while the implants that send collected data will authenticate themselves and are redirected to the "Blot server" and then forwarded to the "Honeycomb" which extracts the data and associates it with the target.
In order to avoid anti-virus software picking up the background activity, the malware implants use fake digital certificates for Kaspersky Lab.
"Digital certificates for the authentication of implants are generated by the CIA impersonating existing entities," WikiLeaks says.
"The three examples included in the source code build a fake certificate for the anti-virus company Kaspersky Laboratory, Moscow pretending to be signed by Thawte Premium Server CA, Cape Town."
This way, if the target tries to inspect the outgoing network traffic, it is likely to mistake the CIA data extraction for a harmless entity.
Conlusion
Yes, the CIA is really doing this. If it were not for brave men (and women) like Julian Assange and his Wikileaks team, we would not have insight into how these organizations are messing with us on a regular basis. Wikileaks has released the complete source code of this project and made it publicly available to forensic experts and anyone interested.
Do you find this information scary? Me too, that is why we need it to be public knowledge. Amazing work, Wikileaks!
Here, check it out yourself: https://wikileaks.org/vault8/#Hive
Information sources: https://wikileaks.org/vault8/#Hive
More Articles like this:
Do you want to learn how Uber deceives regulators?(Read article)
Do you want to know what a former Facebook Exec has to say about it? (Read article)
- Nick ( @cryptonik ) -
