So by sheer dumb luck today, we managed to nab a nice phishing panel and gain access to its backend literally as it got deployed to the internet.
We were monitoring the Certificate Transparency logs for new SSL certs being issued with suspicious domains, and running some quick scans on the ones that triggered a match, when we came across this lovely iCloud phishing page.

So lets step through the scam. After we log into the fake iCloud site, get told our account has been locked! OH NO!

So we click through to verify our apple account, and we get asked for some nice payment information and security questions.
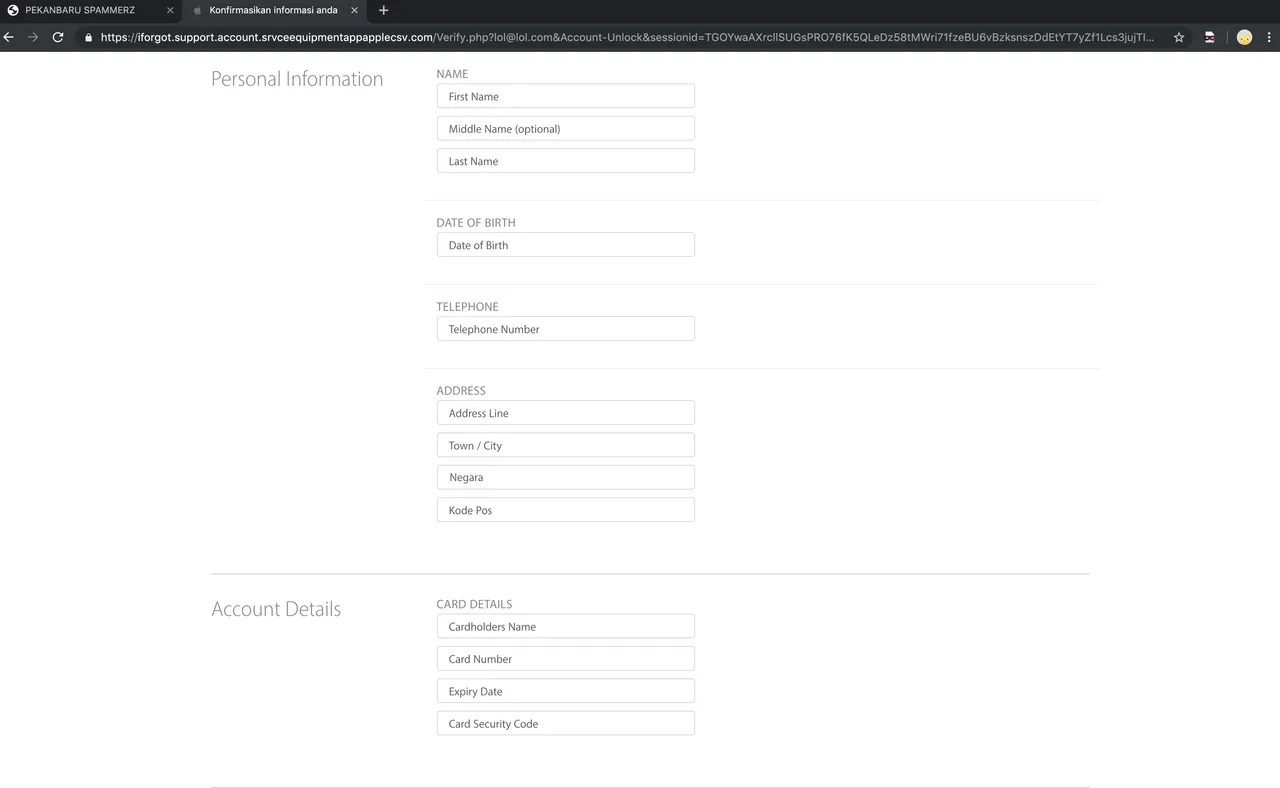
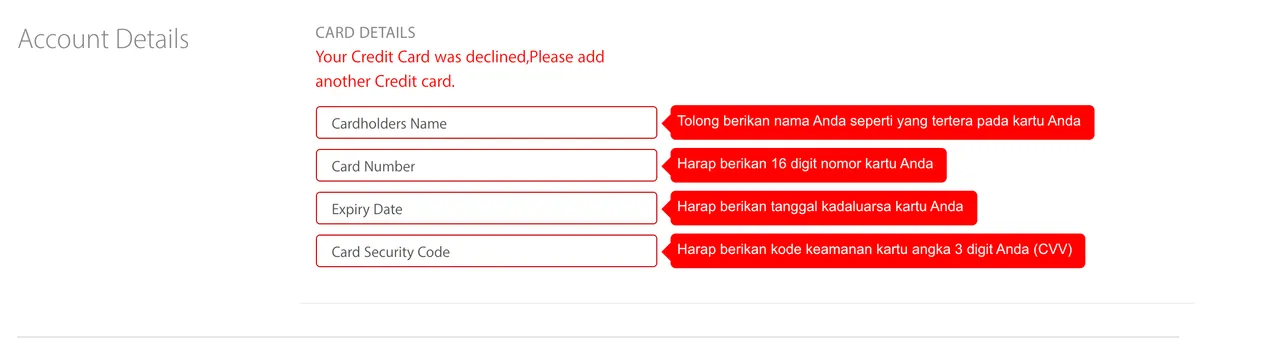
It then tells us our card was declined, and nicely asks us to try another card...
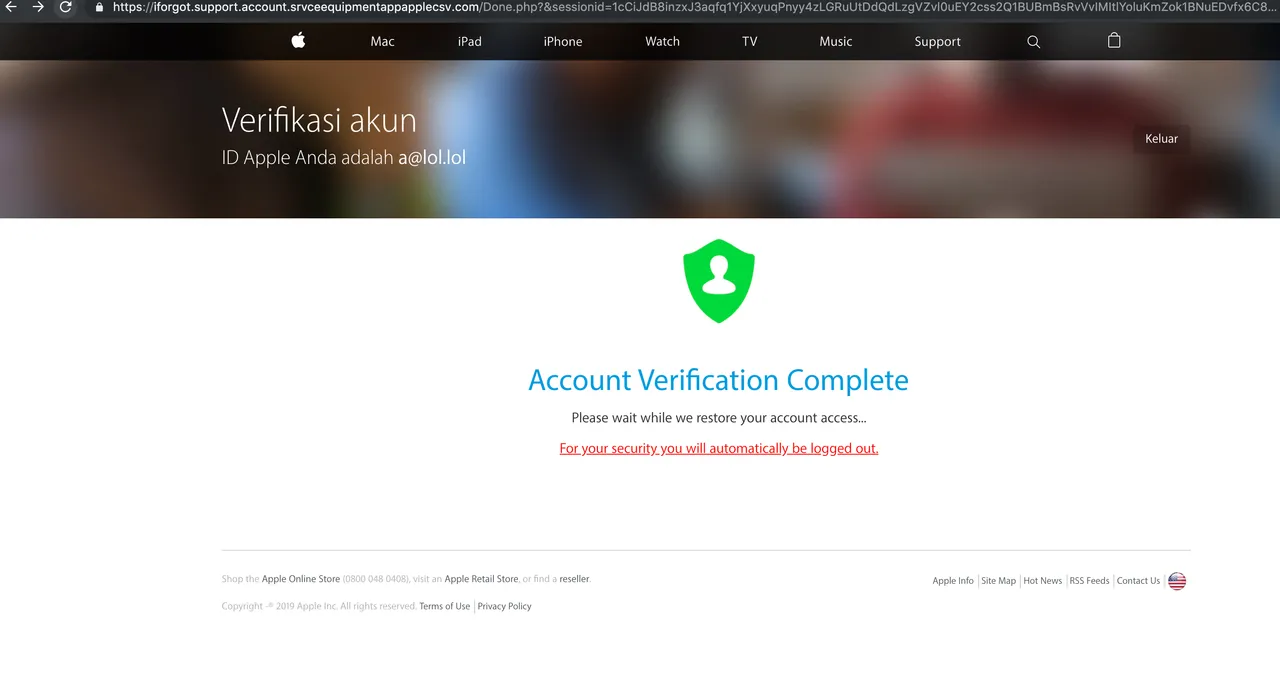
After we submit another card, getting ripped off twice here, we are congratulated with a message telling us its all good now! This page lasts about 5 seconds before we get redirected to the legitimate Apple website.
Luckily, we managed to catch it seconds before it was deployed, and got ahold of a zip file being served from the webroot, named "SCP.zip". We took a quick look inside it, saw it was something we had not seen before, and quickly realized we might be able to actually have a look inside this scam.
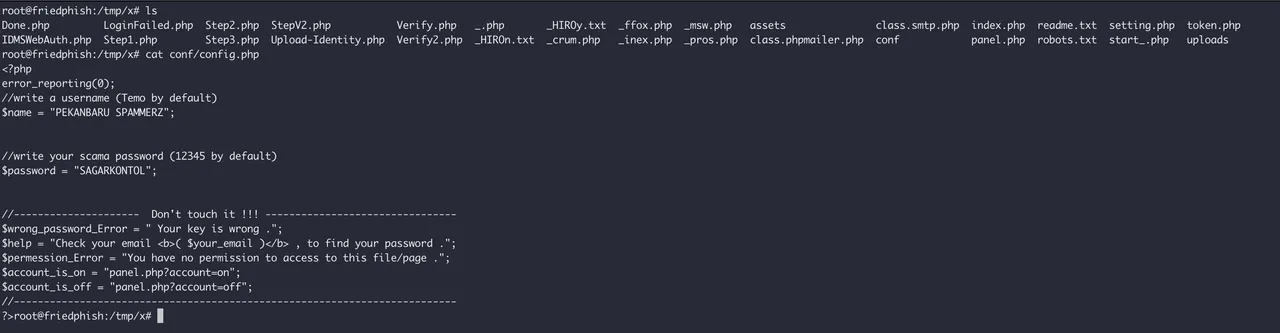
Looks like we got ourselves some login details here, lets go check out panel.php.. It asks us to log in!
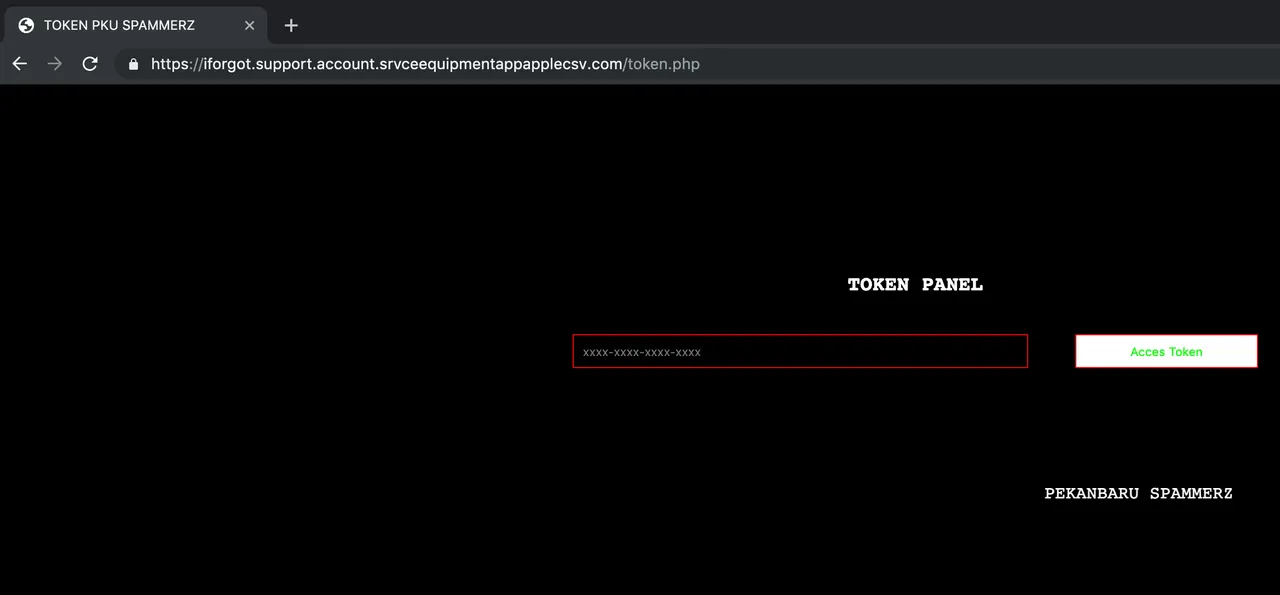
Luckily, we got some tasty credentials from that config file. Lets go log into this mess...
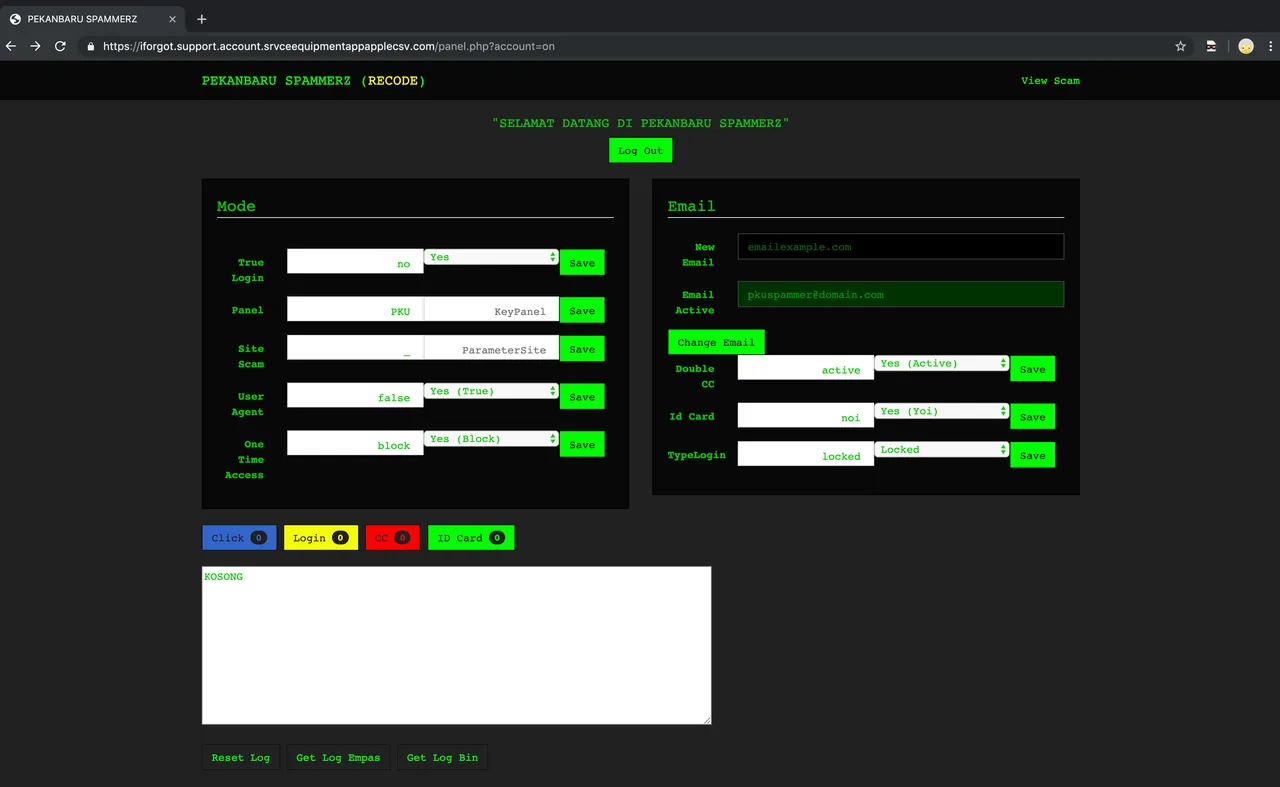
So far there are no victims, but notice how it says "Double CC" is active? This fucking thing literally tries get you to enter your card twice by design, to steal two cards off you. How rude. Luckily, there were not yet any victims, besides our test run, so we cleared the logs and buggered off. I might start logging in at random to wipe their logs and piss them off.
So I've put a copy of this kit up on https://github.com/friedphish/phishkits as usual, my next step I think will be seeing if I can find a way to get code execution via the panel, as the PHP looks fucking horrendously janky and honestly, pwning phishers seems like a fun endeavour.