
To continue our celebration of 10 years of Wikileaks we will be taking a closer look at part 1 of their most recent leaks code-named Vault 7. Vault 7 is a collection of documents and files leaked from an isolated, high-security network situated inside the CIA's Center for Cyber Intelligence in Langley, Virginia, and is the largest ever publication of confidential documents from the CIA. The build up to the publication of Vault 7 was an interesting one, and one that was completely different from their usual publications.
It all started on February 4th 2017 with a cryptic message tweeted from Wikileaks main Twitter account. All it said was What is Vault 7? with a picture of a strange looking building set into the side of a snowy mountain. These cryptic tweets continued over the following 5 days with Where, When, Who, Why and finally How did Vault7 make its way to WikiLeaks?
The first part of Vault 7, called zero day, was finally released on March 7th 2017 and contained 8,761 documents and files exposing the CIA's hacking arsenal of malware, viruses, trojans, weaponized "zero day" exploits, malware remote control systems. Wikileaks press release at the time states:
Vault 7: CIA Hacking Tools Revealed | Wikileaks -03/07/2017
Press Release
This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.
"Year Zero" introduces the scope and direction of the CIA's global covert hacking program, its malware arsenal and dozens of "zero day" weaponized exploits against a wide range of U.S. and European company products, include Apple's iPhone, Google's Android and Microsoft's Windows and even Samsung TVs, which are turned into covert microphones.
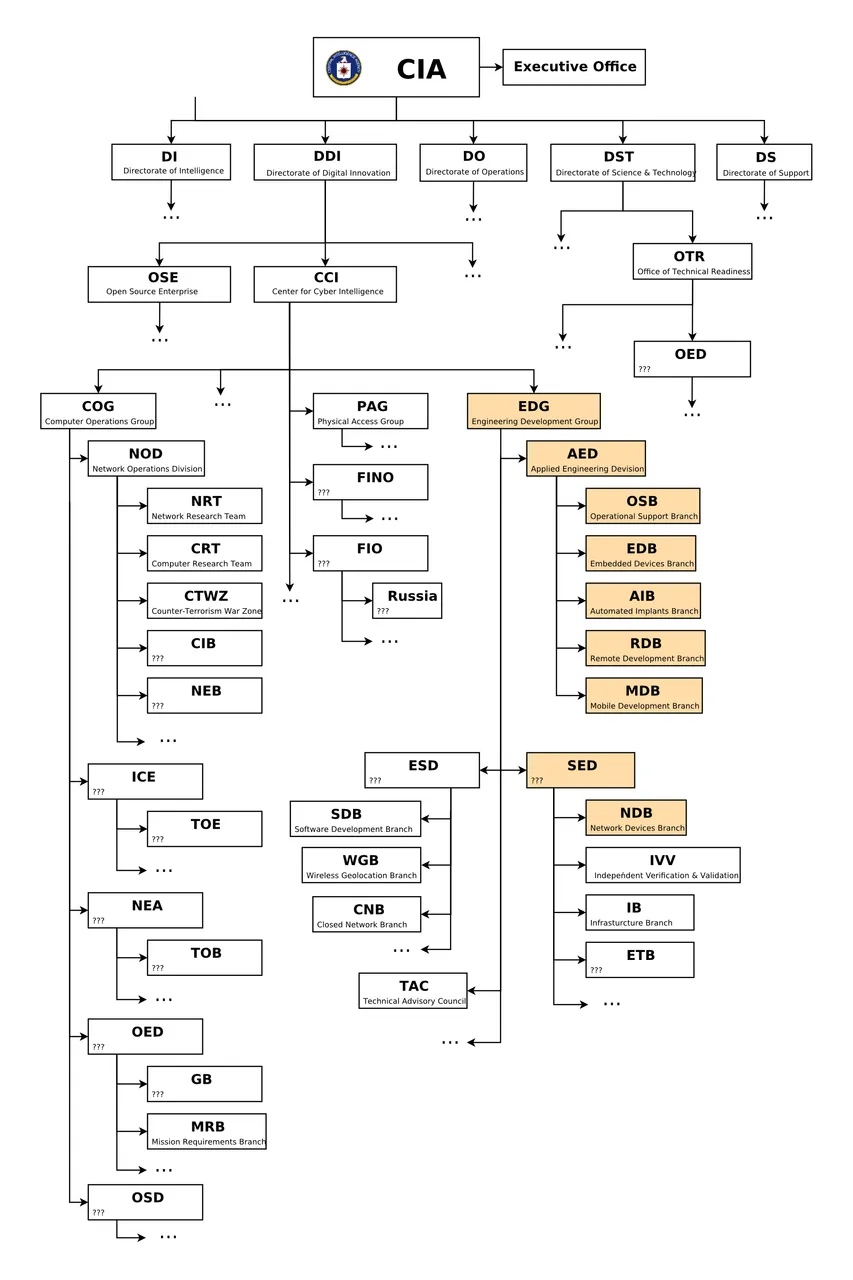
Below is the organization chart mapped out from the documentation and put together by Wikileaks outlining the structure of the CIAs cyber division.
In their press release Wikileaks finally goes on to reassure the public that the Zero Day documents do not include the actual code to the various exploits and malware, thus cannot be used by criminals or other state actors for nefarious activities.
Wikileaks has carefully reviewed the "Year Zero" disclosure and published substantive CIA documentation while avoiding the distribution of 'armed' cyberweapons until a consensus emerges on the technical and political nature of the CIA's program and how such 'weapons' should analyzed, disarmed and published.
Julian Assange Press Conference On The CIA Vault 7 Release | March 9th, 2017

To date there has been 21 different publication from the Vault 7 Zero Day leaks. All of them outlining the various tools and methods used by the CIA to perform covert hacking and surveillance. So far the leaks only described how these tools work and have yet to explain exactly who these tools have been used on and for what purpose, but we can assume they were used on government and private citizens alike. Below is a run down of all the publications:
Dark Matter - 03/27/2017
contains documentation for several CIA projects that infect Apple Mac firmware (meaning the infection persists even if the operating system is re-installed) developed by the CIA's Embedded Development Branch (EDB). These documents explain the techniques used by CIA to gain 'persistence' on Apple Mac devices, including Macs and iPhones and demonstrate their use of EFI/UEFI and firmware malware.
Marble Framework - 03/31/2017
676 source code files for the CIA's secret anti-forensic Marble Framework. Marble is used to hamper forensic investigators and anti-virus companies from attributing viruses, trojans and hacking attacks to the CIA.
Grasshopper - 04/07/2017
27 documents from the CIA's Grasshopper framework, a platform used to build customized malware payloads for Microsoft Windows operating systems.
Hive - 04/14/2017
HIVE is a back-end infrastructure malware with a public-facing HTTPS interface which is used by CIA implants to transfer exfiltrated information from target machines to the CIA and to receive commands from its operators to execute specific tasks on the targets. HIVE is used across multiple malware implants and CIA operations. The public HTTPS interface utilizes unsuspicious-looking cover domains to hide its presence.
Weeping Angel - 04/21/2017
User Guide for CIA's "Weeping Angel" tool - an implant designed for Samsung F Series Smart Televisions. Based on the "Extending" tool from the MI5/BTSS, the implant is designed to record audio from the built-in microphone and egress or store the data.
Scribbles - 04/28/2017
documentation and source code for CIA's "Scribbles" project, a document-watermarking preprocessing system to embed "Web beacon"-style tags into documents that are likely to be copied by Insiders, Whistleblowers, Journalists or others. The released version (v1.0 RC1) is dated March, 1st 2016 and classified SECRET//ORCON/NOFORN until 2066.
Archimedes - 05/05/2017
a tool used by the CIA to attack a computer inside a Local Area Network (LAN), usually used in offices. It allows the re-directing of traffic from the target computer inside the LAN through a computer infected with this malware and controlled by the CIA. This technique is used by the CIA to redirect the target's computers web browser to an exploitation server while appearing as a normal browsing session.
AfterMidnight - 05/12/2017
"AfterMidnight" allows operators to dynamically load and execute malware payloads on a target machine. The main controller disguises as a self-persisting Windows Service DLL and provides secure execution of "Gremlins" via a HTTPS based Listening Post (LP) system called "Octopus".
Athena - 05/19/2017
"Athena" - like the related "Hera" system - provides remote beacon and loader capabilities on target computers running the Microsoft Windows operating system (from Windows XP to Windows 10). Once installed, the malware provides a beaconing capability (including configuration and task handling), the memory loading/unloading of malicious payloads for specific tasks and the delivery and retrieval of files to/from a specified directory on the target system.
Pandemic - 06/01/2017
a persistent implant for Microsoft Windows machines that share files (programs) with remote users in a local network. "Pandemic" targets remote users by replacing application code on-the-fly with a trojaned version if the program is retrieved from the infected machine.
Cherry Blossom - 06/152017
Project of the CIA that was developed and implemented with the help of the US nonprofit Stanford Research Institute (SRI International). CherryBlossom provides a means of monitoring the Internet activity of and performing software exploits on Targets of interest. In particular, CherryBlossom is focused on compromising wireless networking devices, such as wireless routers and access points (APs), to achieve these goals.
Brutal Kangaroo - 06/22/2017
a tool suite for Microsoft Windows that targets closed networks by air gap jumping using thumbdrives. Brutal Kangaroo components create a custom covert network within the target closed network and providing functionality for executing surveys, directory listings, and arbitrary executables.
Elsa - 06/28/2017
A geo-location malware for WiFi-enabled devices like laptops running the Micorosoft Windows operating system. Once persistently installed on a target machine using separate CIA exploits, the malware scans visible WiFi access points and records the ESS identifier, MAC address and signal strength at regular intervals. To perform the data collection the target machine does not have to be online or connected to an access point; it only needs to be running with an enabled WiFi device.
OutlawCountry - 06/29/2017
Allows for the redirection of all outbound network traffic on the target computer to CIA controlled machines for ex- and infiltration purposes. The malware consists of a kernel module that creates a hidden netfilter table on a Linux target; with knowledge of the table name, an operator can create rules that take precedence over existing netfilter/iptables rules and are concealed from an user or even system administrator.
BothanSpy - 07/06/2017
an implant that targets the SSH client program Xshell on the Microsoft Windows platform and steals user credentials for all active SSH sessions. These credentials are either username and password in case of password-authenticated SSH sessions or username, filename of private SSH key and key password if public key authentication is used.
Highrise - 07/13/2017
An Android application designed for mobile devices running Android 4.0 to 4.3. It provides a redirector function for SMS messaging that could be used by a number of IOC tools that use SMS messages for communication between implants and listening posts. HighRise acts as a SMS proxy that provides greater separation between devices in the field ("targets") and the listening post (LP) by proxying "incoming" and "outgoing" SMS messages to an internet LP.
UCL / Raytheon - 07/19/2017
documents from the CIA contractor Raytheon Blackbird Technologies for the "UMBRAGE Component Library" (UCL) project. The documents were submitted to the CIA between November 21st, 2014 (just two weeks after Raytheon acquired Blackbird Technologies to build a Cyber Powerhouse) and September 11th, 2015. They mostly contain Proof-of-Concept ideas and assessments for malware attack vectors - partly based on public documents from security researchers and private enterprises in the computer security field.
Imperial - 07/27/2017
A selections of 3 tools.
Achilles is a capability that provides an operator the ability to trojan an OS X disk image (.dmg) installer with one or more desired operator specified executables for a one-time execution.
Aeris is an automated implant written in C that supports a number of POSIX-based systems (Debian, RHEL, Solaris, FreeBSD, CentOS).
SeaPea is an OS X Rootkit that provides stealth and tool launching capabilities. It hides files/directories, socket connections and/or processes.
Dumbo - 08/03/2017
capability to suspend processes utilizing webcams and corrupt any video recordings that could compromise a PAG deployment. The PAG (Physical Access Group) is a special branch within the CCI (Center for Cyber Intelligence); its task is to gain and exploit physical access to target computers in CIA field operations.
CouchPotato - 08/10/2017
a remote tool for collection against RTSP/H.264 video streams. It provides the ability to collect either the stream as a video file (AVI) or capture still images (JPG) of frames from the stream that are of significant change from a previously captured frame. It utilizes ffmpeg for video and image encoding and decoding as well as RTSP connectivity. CouchPotato relies on being launched in an ICE v3 Fire and Collect compatible loader.

So there we have it. All of the CIA's hacking tools and exploits so far. It's really is incredible the amount of tools and code they have built up over the years. The amount of man power invested into this must be immense, all paid for by the US tax payer. The CIA would argue that these tools are used strictly to monitor criminals and terrorists for the sake of national security. But as we saw in the initial Vault 7 pre-release in February the CIA used human and electronic spies to spy on the French 2012 presidential election.
In tomorrows edition of Wikileaks Week we will be taking a look back over the last 12 months of Wikileaks, and particularly their editor Julian Assange, and will be exploring some of the highlights, struggles, and attacks from the media and governments that they've had to endure over the last year.
Previous Wikileaks Week Posts:
WIKILEAKS WEEK DAY 1 | The Leaks

